12-18-2020, 07:15 PM
Try to use only these 6 Ciphers, in this exact order:
The last two are weak, according to SSLLABs, but they are needed for SAFARI 6, 7, 8 and Windows Phone 8. If you don't need them, you can remove the last 2 Cipher's.

There is a list of Clients that will not be able to access, image below:
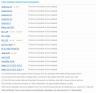
List of Clients that will be able to access using only TLS 1.2 with STRONG CRYPTO

Code:
ECDHE-RSA-AES256-GCM-SHA384:
ECDHE-RSA-AES128-GCM-SHA256:
DHE-RSA-AES256-GCM-SHA384:
DHE-RSA-AES128-GCM-SHA256:
ECDHE-RSA-AES256-SHA384:
ECDHE-RSA-AES128-SHA256The last two are weak, according to SSLLABs, but they are needed for SAFARI 6, 7, 8 and Windows Phone 8. If you don't need them, you can remove the last 2 Cipher's.
There is a list of Clients that will not be able to access, image below:
List of Clients that will be able to access using only TLS 1.2 with STRONG CRYPTO